Created: 11/07/2024 07:06 Last Updated: 11/07/2024 07:10
⭐ This alert is prepared for the ‘How to Investigate a SIEM Alert’ course. If you haven’t taken the course yet, please complete it first.
EventID : 257 Event Time : May, 13, 2024, 09:22 AM Rule : SOC282 - Phishing Alert - Deceptive Mail Detected Level : Security Analyst SMTP Address : 103.80.134.63 Source Address : free@coffeeshooop.com Destination Address : Felix@letsdefend.io E-mail Subject : Free Coffee Voucher Device Action : Allowed
Parse Email

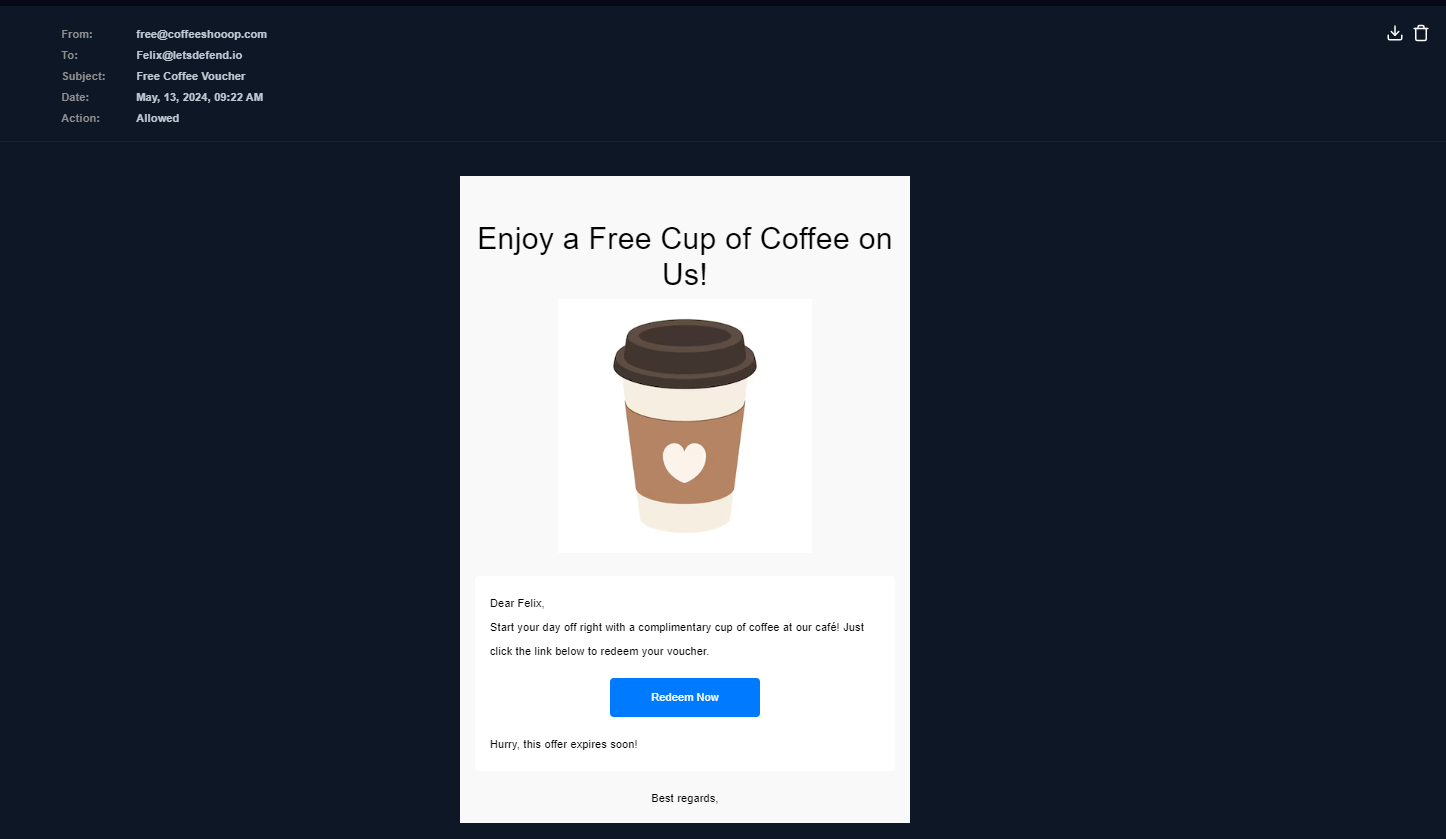
Lets go to Email Security and find this email first then we can see that this is obviously a phishing email from sender email to file attachment
When was it sent? : May, 13, 2024, 09:22 AM
What is the email's SMTP address? : 103.80.134.63
What is the sender address? : free@coffeeshooop.com
What is the recipient address? : Felix@letsdefend.io
Is the mail content suspicious? : Yes
Are there any attachment? : Yes
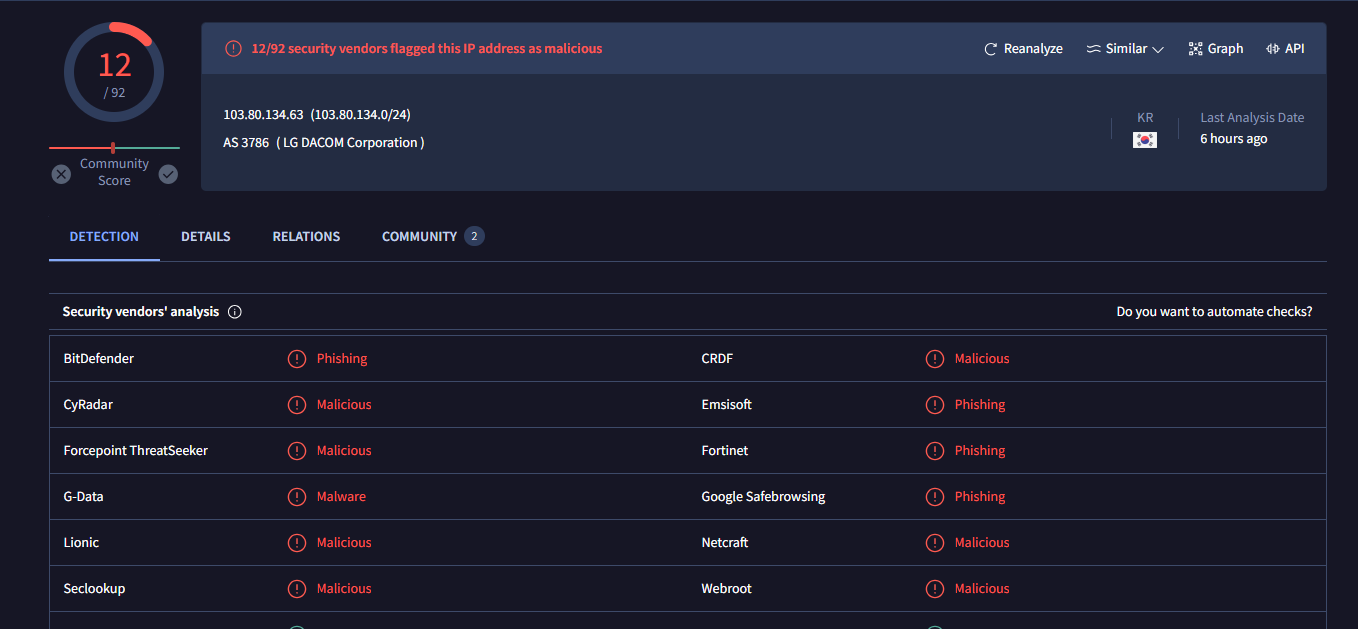
I also searched for the SMTP address of the sender which was flagged by 12 different security vendors
Are there attachments or URLs in the email?
Yes
Analyze Url/Attachment
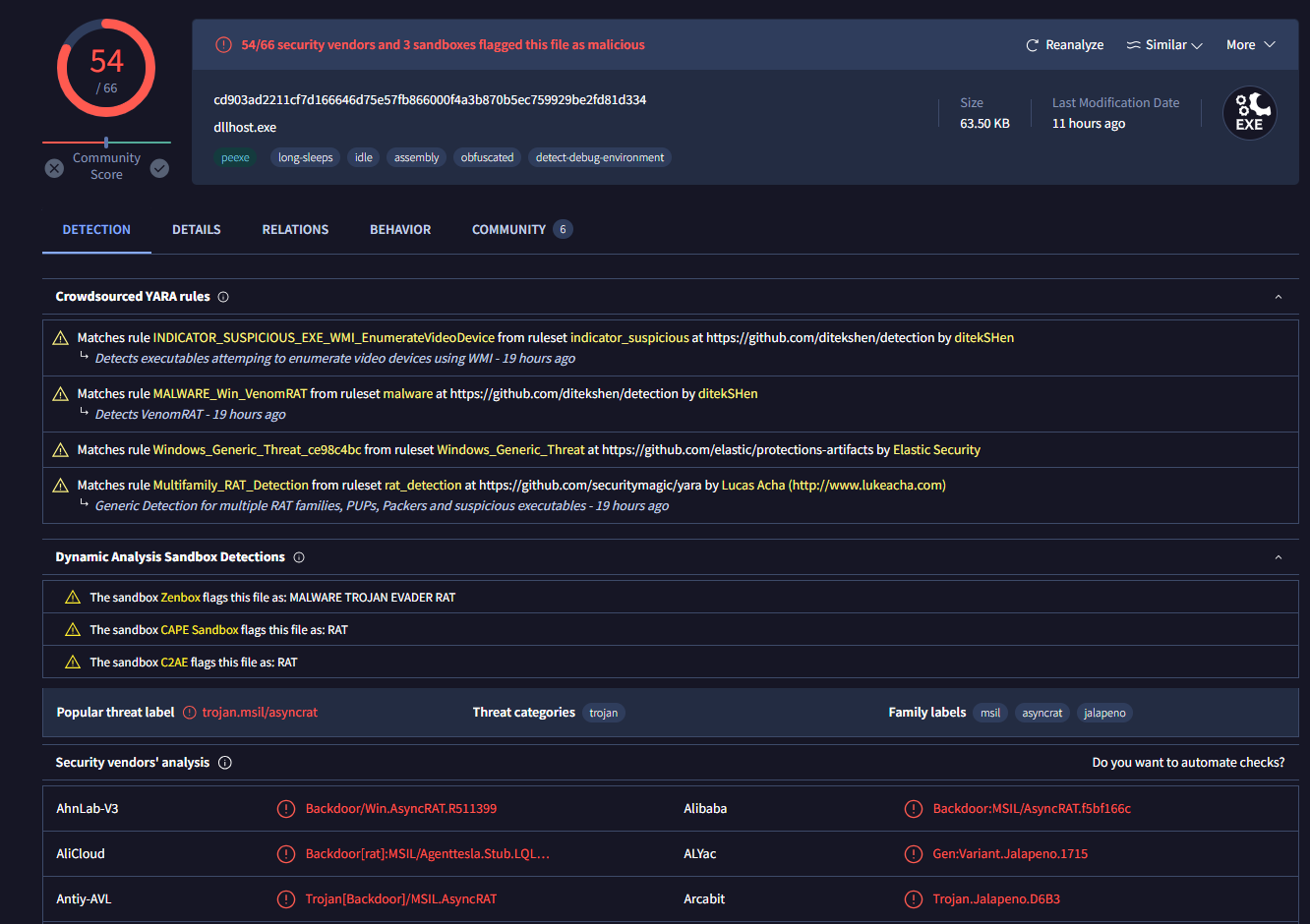
After searching filehash on VirusTotal, we can see that this attachment is an infamous AsyncRAT (Asynchronous Remote Access Trojan) malware so we did not need to think twice and answer this as "Malicious"
Malicious
Check If Mail Delivered to User?
Alert details tell us that this mail was allowed so we need to check the endpoint to check if the file was downloaded and executed
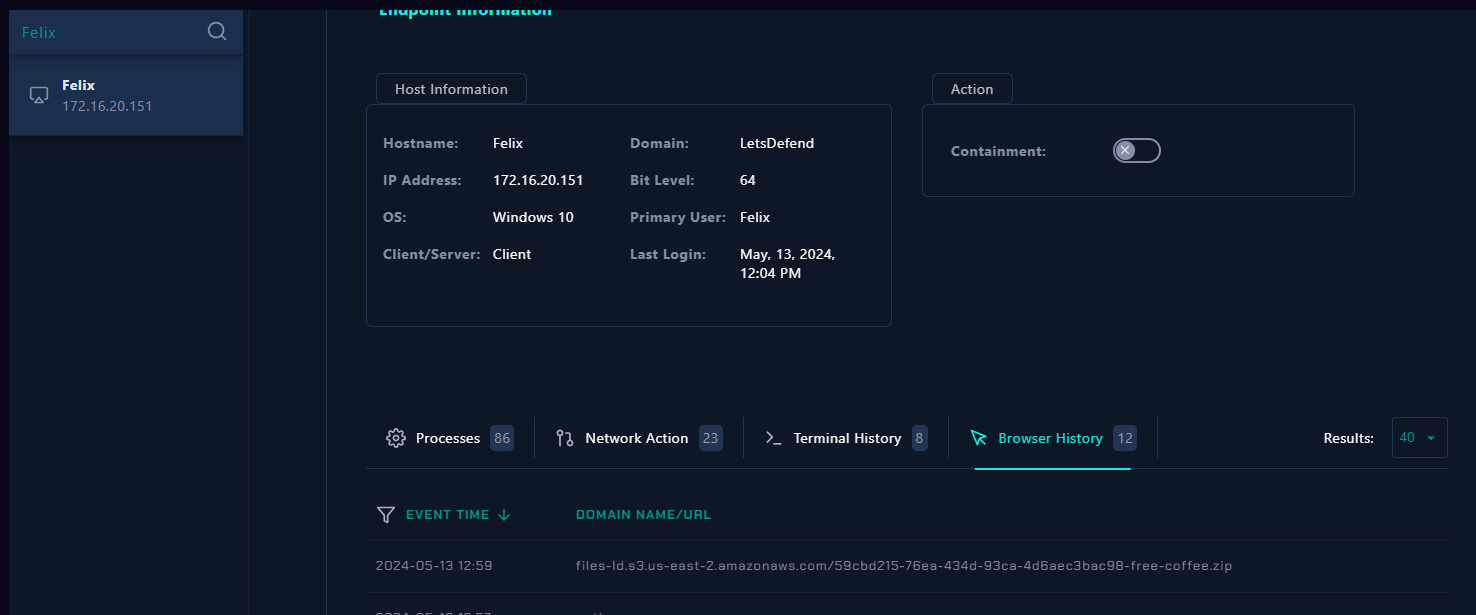
Upon investigation on the Felix's endpoint when we checked on Browser History, we will see an url to download this malware so now its confirmed that mail was successfully delivered malware to the user
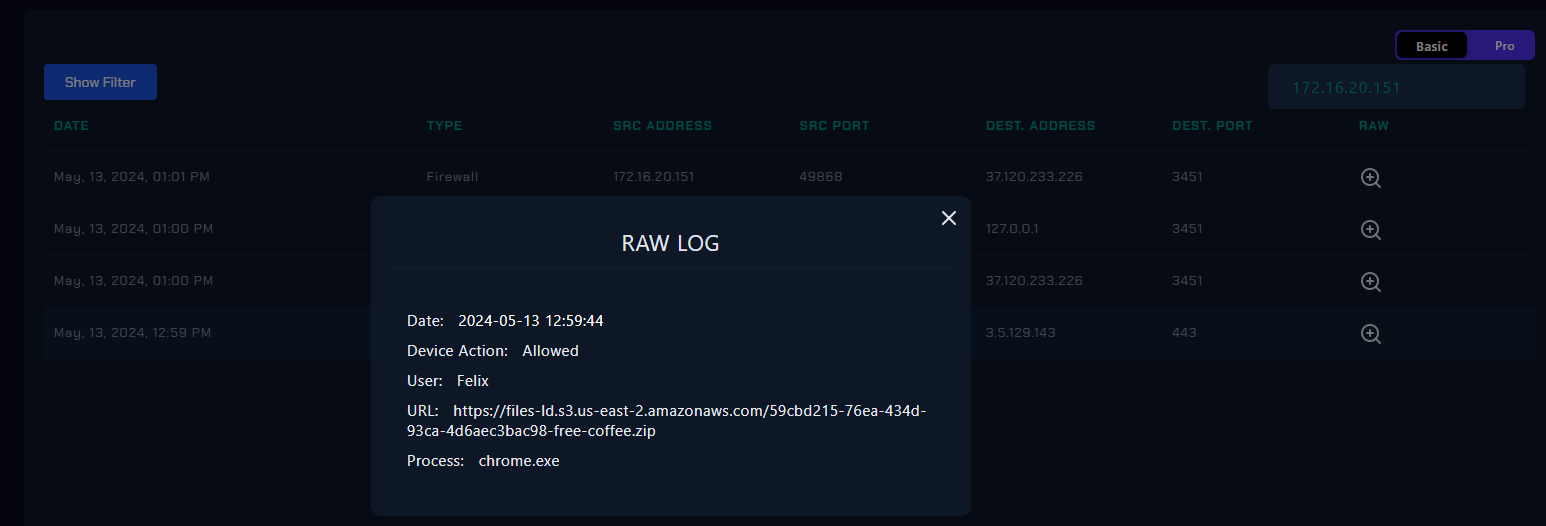
On Log Management, we can see that user downloaded this malware using Google Chrome
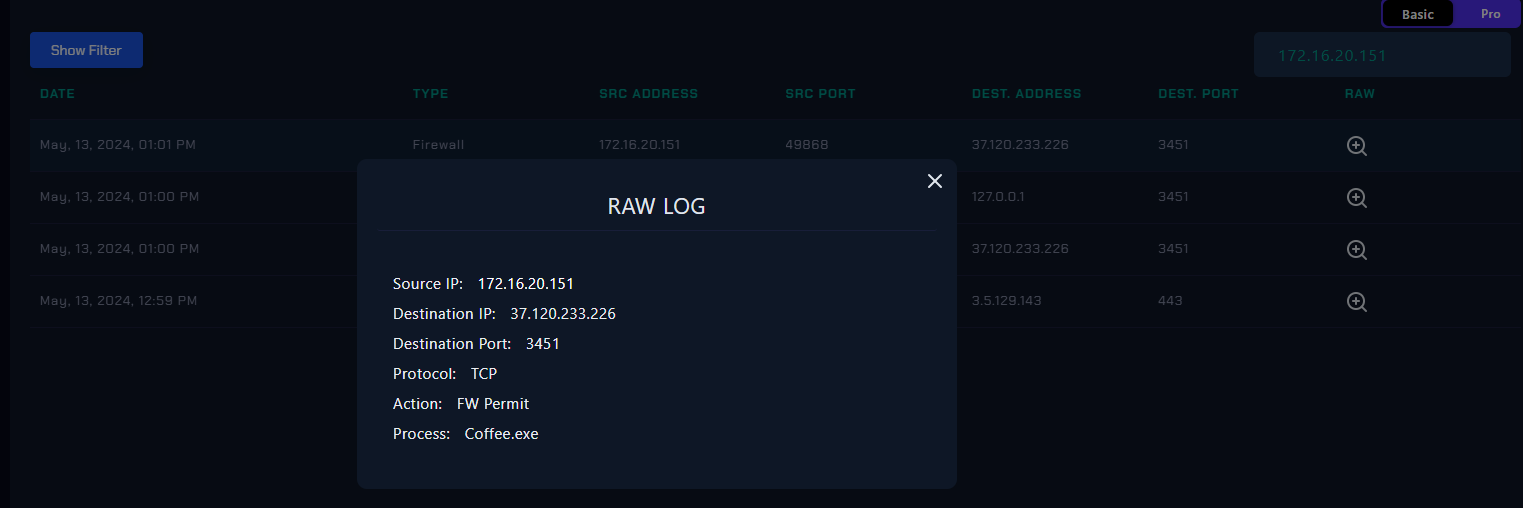
After that we can see another log from Felix to C2 server which we can also see the process that responsible for this connection
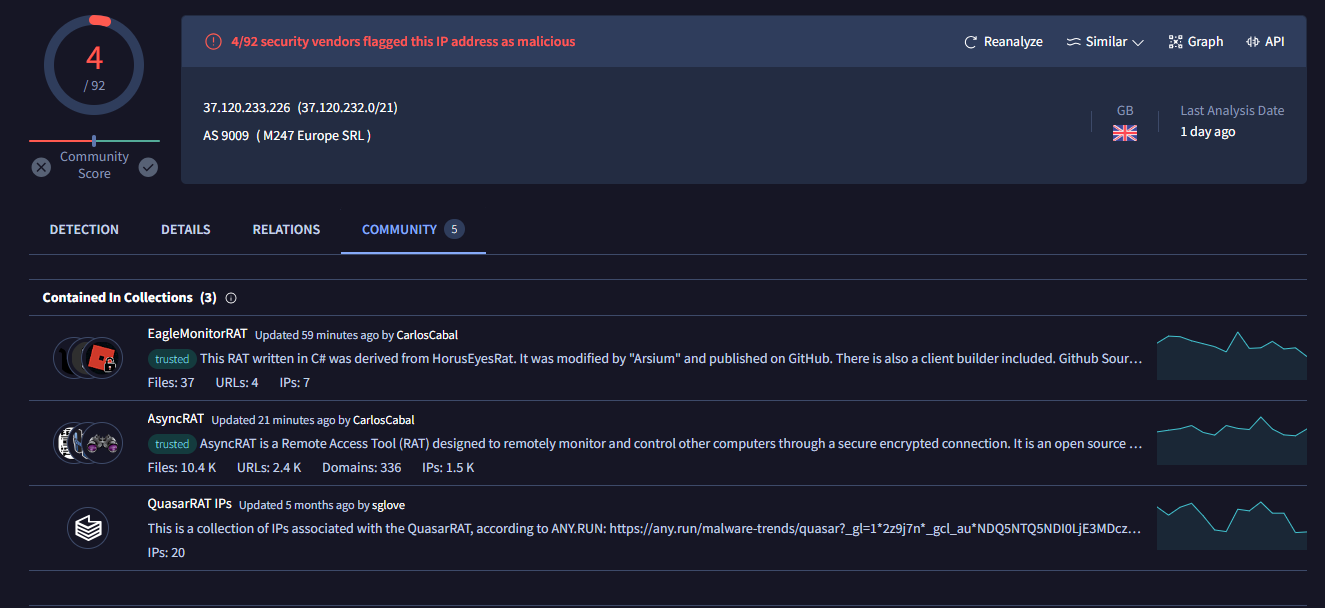
After searching for this IP address on VirusTotal, we can see that this IP address also used for multiple RAT, not just AsyncRAT
Delivered
Delete Email From Recipient!
Check If Someone Opened the Malicious File/URL?
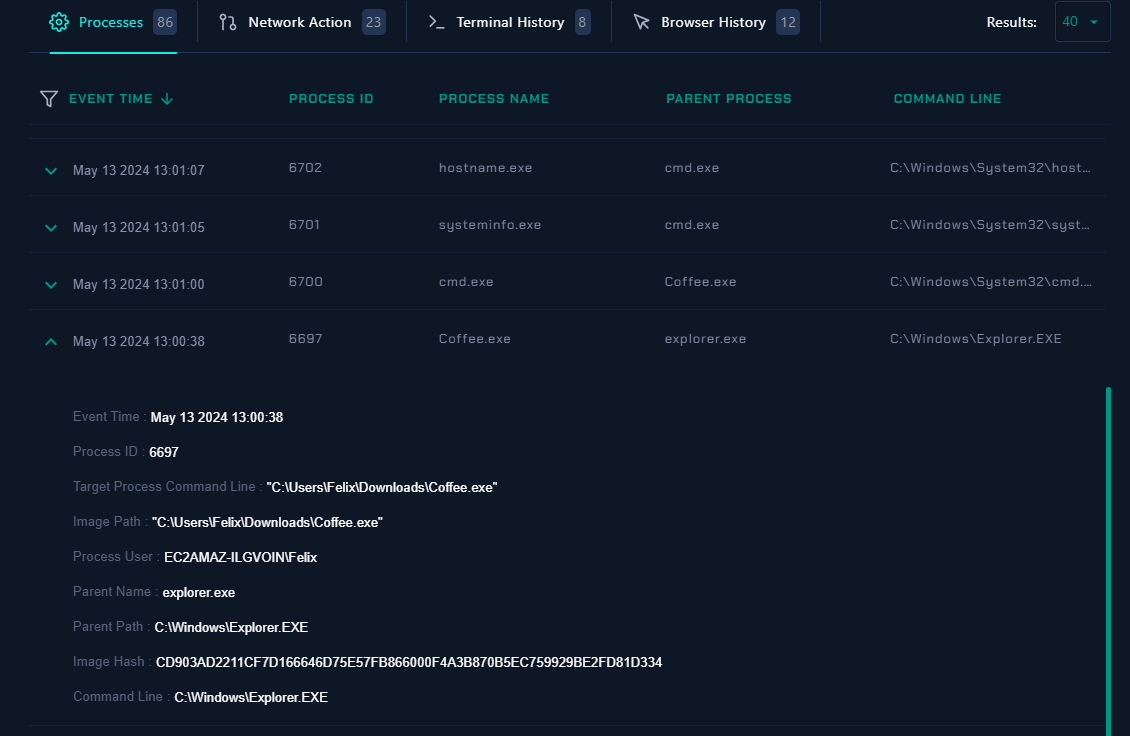
Look a little bit further into processes on Felix's endpoint, we can see the malicious process is running and its a child process of explorer.exe indicating malware was executed by user himself
and after looking other processes, we can see cmd.exe is a child process of Coffee.exe and there are several processes that spawned after cmd.exe
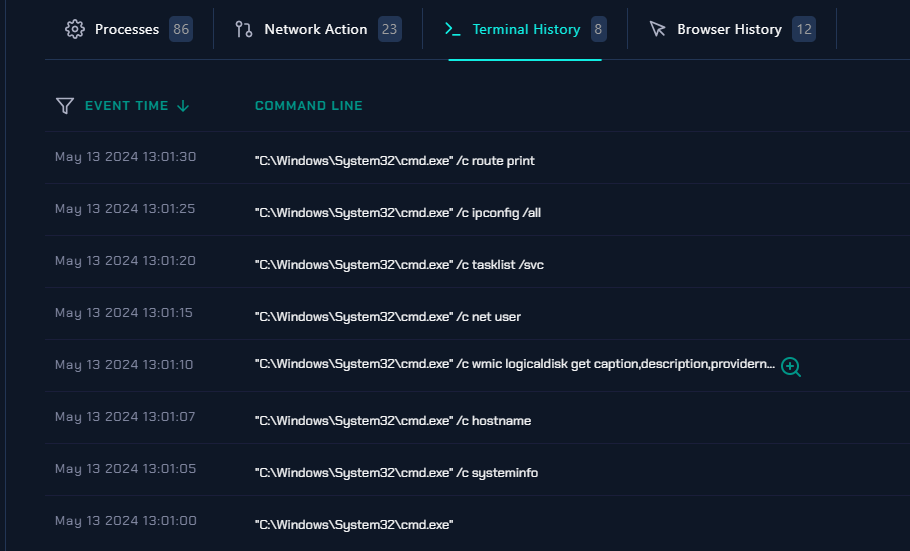
By taking a look at Terminal History, we can see how many commands were executed and most of them is about recon/gathering information on infected system (Felix's Endpoint)
Opened
Containment
Add Artifacts
free@coffeeshooop.com
coffeeshooop.com
103.80.134.63
37.120.233.226
files-ld.s3.us-east-2.amazonaws.com/59cbd215-76ea-434d-93ca-4d6aec3bac98-free-coffee.zip
961d8e0f1ec3c196499bfcbd0a9d19fa
Analyst Note
Phishing mail was detected and was not blocked by firewall or other security measures, which lead to user downloaded AsyncRAT malware and executed it and after that a new connection was established to C2 server and executed command using `cmd.exe` to gather information on the infected system.
Email was deleted and host is contained upon uncovering these facts so the next step would be eradicating malware and recovery process and then after that a lesson learned process need to be conducted to prevent future incidents like this from happening again.
Editor's Note: Security Report